What if hackers could access your thoughts, control your actions, or even change your emotions? Brain-computer interfaces (BCIs) like Neuralink are here, and so are the cyber threats. Experts say the concept of "hacking the brain" is no longer science fiction. Learn how neural hacking is turning sci-fi into reality and what's at stake for your sensitive neural data. Stay safe out there! #NeuralHacking #BCISecurity #MindControl #TechRisks
____
🎯 Welcome to CISO Marketplace — Your Grassroots Hub for Cybersecurity Tools, Threat Awareness & Startup Innovation
We’re building a thriving ecosystem for cybersecurity professionals, founders, and curious minds. From microtools and policy generators to indie product reviews and breach analysis, we empower the infosec community with hands-on, actionable content.
🌐 Explore More
🔗 Website: https://www.cisomarketplace.com
🔐 Security Intelligence: https://quantumsecurity.ai
📲 Follow Us on Social Media
X (Twitter), TikTok, Pinterest: @CISOMarketplace
Partner Channel: @ScamWatchHQ (fraud & scam investigations)
☕ Support Our Mission
Your support helps keep our tools and education free and open to all:
💸 Buy Us a Coffee: https://coff.ee/cisomarketplace
🪙 Donate Crypto: https://coindrop.to/cisomarketplace
📢 Hashtags to Help You Find Us
#cybersecurity #infosec #breach #privacy #hacking #CISO #ransomware #cyberawareness #zerotrust #cyberresilience
Show More Show Less View Video Transcript
0:00
You know, for all of human history, our
0:02
own minds have been the one truly
0:04
private place, a fortress that no one
0:07
could get into. But what happens when we
0:09
decide to build a bridge into that
0:10
fortress, a direct line from our
0:12
thoughts to the digital world? And what
0:15
happens when someone else figures out
0:16
how to cross that bridge? Just think
0:18
about that for a second. What if you
0:20
could write an email just by thinking
0:22
the words? Or, I don't know, steer a
0:25
wheelchair with nothing but your mind.
0:27
This this isn't science fiction anymore.
0:30
This is the incredible promise of a
0:32
technology that is right now becoming a
0:35
reality. Okay, so let's get on the same
0:37
page. A brain computer interface or BCI
0:41
is pretty much exactly what it sounds
0:43
like. It's a system that records the
0:45
tiny electrical signals zipping between
0:47
your neurons, your brain waves, and then
0:49
uses some seriously powerful algorithms
0:52
to translate them into commands for a
0:54
computer. It is quite literally the
0:56
ultimate hands-free device. And the
0:58
potential here, it's just staggering. I
1:01
mean, we are talking about giving
1:02
movement back to people who are
1:04
paralyzed. Giving a voice to those who
1:06
can't speak, letting someone control an
1:09
advanced prosthetic limb as if it were
1:10
their own. But it goes way beyond just
1:13
medical uses. This could completely
1:15
change how we interact with, well,
1:18
everything. enhancing our own minds,
1:20
creating virtual reality experiences so
1:22
real you can't tell the difference. The
1:24
list goes on. And this isn't some pie in
1:27
the sky faroff future. It's happening
1:30
now. In January of 2024, Elon Musk's
1:34
company, Neurolink, announced that it
1:36
had successfully implanted its first
1:39
wireless BCI into a human being. The
1:42
patient is apparently doing great, and
1:44
the device is already detecting neuron
1:46
activity. The future has officially
1:49
arrived. This quote from Elon Musk just
1:51
nails the ambition behind all of this.
1:54
The goal isn't just to fix something
1:56
that's broken. It's about going beyond
1:58
our natural limits. The thought of
2:00
giving a mind like Steven Hawkings the
2:02
power to communicate at the speed of
2:03
thought. I mean, that's just an
2:05
incredibly powerful and inspiring
2:07
vision. But here's the thing. Every new
2:10
connection creates a new weak spot, a
2:12
new vulnerability. What if this direct
2:15
line into the brain could be
2:17
compromised? What if it could be
2:18
hijacked? The very same technology that
2:21
promises to set us free could also be
2:24
used to control us. And folks, this
2:26
isn't just some hypothetical fear
2:28
anymore. It's a security flaw that has
2:30
already been proven to work. Now, here's
2:32
what's so wild about this. For years,
2:34
everyone worried about hacking the
2:36
software or the data stream from the
2:38
BCI. But researchers at MIT, they found
2:42
something totally different. They found
2:44
a vulnerability in the physical hardware
2:46
itself. They figured out a way to get
2:49
inside the system remotely before the
2:51
data even gets processed. So, how does
2:54
this brain hack even work? Well, it's
2:56
actually kind of simple, which is what
2:58
makes it so scary. An attacker just
3:00
blasts out a specific AM radio signal,
3:03
you know, like an old car radio. It
3:05
turns out the unshielded wires on these
3:07
BCI headsets, they act as perfect little
3:10
antennas. They pick up that signal and
3:12
the devices's own amplifier gets
3:14
tricked. It accidentally interprets that
3:16
radio wave as a real brain wave,
3:18
injecting a fake command right into the
3:21
system. And the results, they're pretty
3:22
dramatic. In one of the most powerful
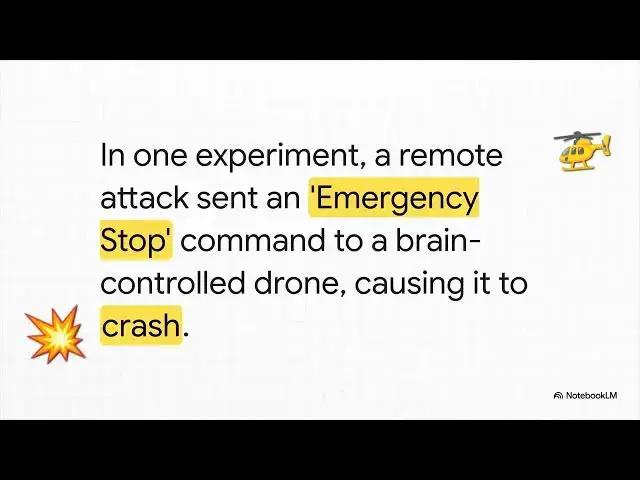
3:25
tests, the MIT team took aim at a BCI
3:27
that was being used to fly a drone. By
3:30
injecting a signal that meant emergency
3:31
stop, they could override the user's
3:34
thoughts and send the drone crashing
3:36
right out of the sky. This isn't just
3:38
messing with data on a screen. This is
3:40
causing realworld physical damage. In
3:43
the drone was just the warm-up act. The
3:45
team showed just how versatile this
3:47
attack really is. They hijacked a
3:49
virtual keyboard, forcing someone who
3:51
was trying to think the word love to
3:53
type hate instead. They tricked a
3:55
popular meditation app into thinking a
3:57
user was in a deep calm state when their
3:59
eyes were wide open. And what's really
4:01
crucial here is they proved this hack
4:03
works on everything from super expensive
4:05
research devices to cheap consumer
4:07
gadgets. And this is where the academic
4:10
threat gets real. It gets personal. As
4:13
one person put it on a Reddit forum
4:15
discussing this very thing, they said,
4:17
"You could just flood the system with
4:19
noise. Think of it," they wrote, like
4:21
someone screaming inside your skull. And
4:24
that that just perfectly captures the
4:26
absolute horror of this kind of
4:28
violation. But here's the really scary
4:30
part. This brain hack, it's not a
4:32
one-off problem. It's really just the
4:35
next step in a long and pretty troubling
4:37
history of security holes found in
4:39
critical medical devices. Devices that
4:42
are connected directly to our bodies.
4:44
And just look at this timeline. This
4:46
isn't a new problem. This has been
4:48
building for more than a decade. We're
4:51
talking a researcher hawking his own
4:53
insulin pump back in 2011. It even
4:55
reached the White House in 2013 when
4:58
Vice President Dick Cheneyy's doctors
5:00
had to disable the wireless feature on
5:02
his defibrillator specifically to
5:04
prevent an assassination attempt via
5:06
hacking. Since then, it's just been one
5:08
thing after another. Vulnerable insulin
5:10
pumps, massive pacemaker recalls. The
5:13
pattern is undeniable. And looking
5:15
ahead, the threats are just getting
5:17
smarter. Experts are now warning us
5:19
about things like AI powered attacks
5:21
that can actually learn your unique
5:23
brain signals to create custom hacks
5:26
that are almost impossible to detect or
5:28
how future quantum computers could just
5:30
shatter the encryption we use to protect
5:32
our data today. And that's not even
5:34
getting into old school threats like a
5:36
malicious employee or even worse neural
5:38
spyware. An app that doesn't try to
5:40
control you but just listens, reading
5:43
your private thoughts, your biases, your
5:46
secrets. Okay, but it's not all doom and
5:48
gloom. It's not. Because in the face of
5:51
these incredible risks, there is a race
5:54
happening right now on multiple fronts
5:57
to build the defenses we're going to
5:58
need. A race to build a firewall for the
6:01
human mind itself. And it's being fought
6:04
by engineers, lawmakers, and even
6:06
philosophers. So, on the engineering
6:08
front, for every vulnerability, there's
6:10
a potential countermeasure. The fixes
6:12
for that radio hack are actually pretty
6:14
straightforward. problem. Unshielded
6:16
cables. Solution: Use shielded ones.
6:19
Simple. Attackers using one fixed radio
6:21
frequency. Okay, fine. We'll just have
6:23
the device constantly hop between
6:25
different frequencies. An even clever
6:27
idea is personalizing the BCI to your
6:29
unique brain wave phase or timing. That
6:31
way, the device knows the difference
6:33
between a real thought from you and a
6:35
fake one from an attacker. The point is,
6:37
the technical fixes are there. The
6:39
second front in this race is legal. All
6:41
around the world, lawmakers are
6:43
scrambling to figure out how to regulate
6:45
this stuff. And it's leading to these
6:46
fascinating brand new legal ideas like
6:49
neurorites or classifying neural data as
6:52
its own special highly sensitive
6:54
category of information. And it's really
6:56
interesting to see the different ways
6:57
people are tackling it. Chile went allin
7:00
becoming the first country on earth to
7:02
actually write neuroites into its
7:04
constitution. Here in the US, Colorado
7:07
was the first state to say, "Nope, you
7:09
can't collect this data without explicit
7:11
opt-in consent. California followed suit
7:14
with a slightly weaker law. And
7:16
meanwhile, the European Union is trying
7:17
to fit it into their existing GDPR
7:19
rules, basically treating your brain
7:21
data like any other health data." But
7:23
that brings us to the third front in
7:25
this race. And it might be the hardest
7:27
one of all, the ethical one. What about
7:30
the questions that technology and laws
7:32
just can't answer? This tech forces us
7:35
to ask these incredibly deep questions
7:37
we've never really had to face before.
7:40
Like, what does cognitive privacy even
7:42
mean? Do you have a right to keep your
7:44
own thoughts private? And this quote
7:46
just hits so hard. Philosophers have
7:49
always said that your mind is the last
7:51
refuge of freedom. They could imprison
7:53
your body, but your thoughts, your
7:55
thoughts were always yours. With BCIs,
7:58
for the first time in human history,
8:00
that is no longer a guarantee. Which
8:02
brings this whole massive complicated
8:05
conversation down to one final and very
8:08
personal question. As this technology
8:10
moves out of the lab and into our lives,
8:12
it all comes down to a simple powerful
8:15
question of control. Who owns your mind?
8:18
At the end of the day, the core tension
8:20
is crystal clear. On one hand, you have
8:23
this technology with almost godlike
8:25
power to restore and revolutionize human
8:28
life. And on the other hand, you have a
8:30
security risk so deep that it threatens
8:33
the very thing that makes you you. Your
8:35
identity, your freedom, your
8:37
consciousness. So I'll just leave you
8:39
with this final thought. As this
8:41
technology becomes our reality, we have
8:44
to decide who's really in charge. Is it
8:47
the engineers, the companies, the
8:49
governments, or is it you? Who gets to
8:52
write the user agreement for your mind?
#Hacking & Cracking